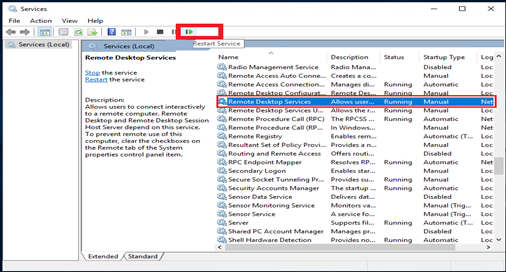
One protective layer to take into account while hardening your Windows Server is the TLS security that Windows Remote Desktop Protocol offers.
Prerequisite for Configuration of TLS Certificate:
- Make sure your Windows Server instance has a DNS A record added.
- The web server is running on Port 80.
Configuration of TLS Certificate:
- Install Chocolatey. Software package installation, updates, and management can be made easier for Windows users with the help of Chocolatey, a package manager. Developers, system administrators, and power users all choose Chocolatey because it offers a practical and effective approach to manage software packages on Windows machines. To do this follow the steps below.
- Open an administrative PowerShell. Click Start, type PowerShell, right-click Windows PowerShell, and then click Run as administrator.
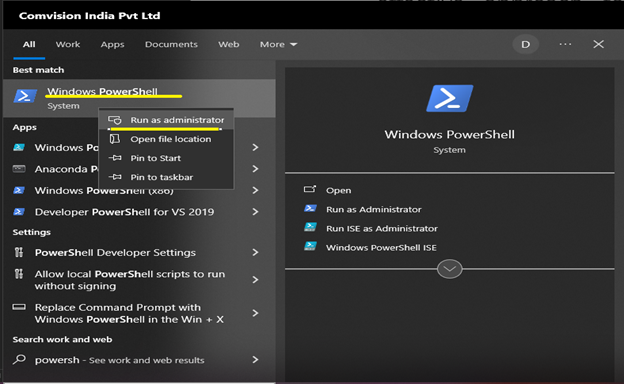
- Run the command below:
set-ExecutionPolicy Bypass -Scope Process -Force; [System.Net.ServicePointManager]::SecurityProtocol = [System.Net.ServicePointManager]::SecurityProtocol -bor 3072; iex ((New-Object System.Net.WebClient).DownloadString(‘https://chocolatey.org/install.ps1’))
2. Relog in to the server after installing Chocolatey to allow the new environment to take effect.
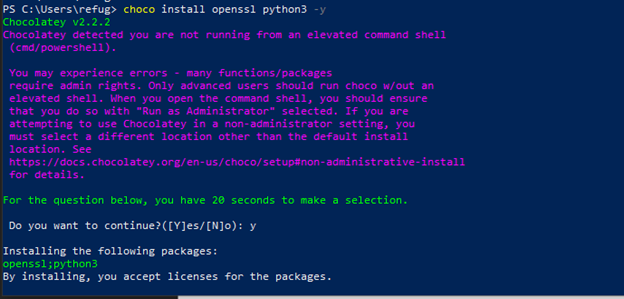
3. Use Chocolatey to install Python 3 and OpenSSL
- choco install openssl python3 -y
4. Use pip to install Certbot.
- pip install certbot
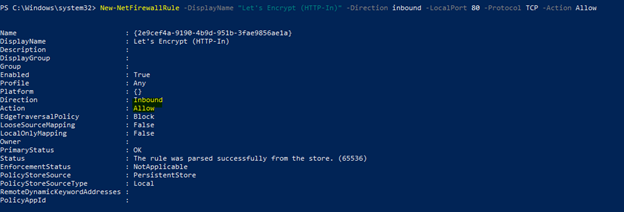
5. Verify that port 80 is open; if not, allow inbound traffic to it.
- New-NetFirewallRule -DisplayName “Let’s Encrypt (HTTP-In)” -Direction inbound -LocalPort 80 -Protocol TCP -Action Allow
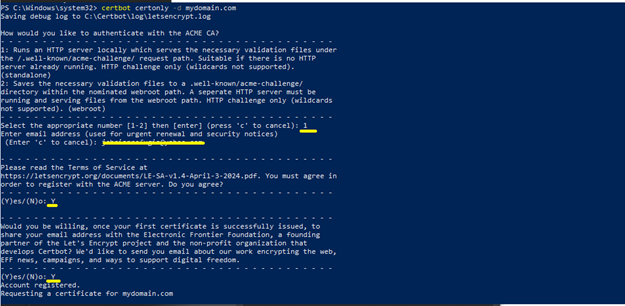
6. Obtain a Certificate for Let’s Encrypt. Assuming we are using domain name “mydomain.com”. Follow the question prompted as below.
- certbot certonly -d mydomain.com
7. After you obtained certificate from step 6. The keys are save in C:\Certbot\live\mydomain.com. Windows requires the.pfx format for certificates, but we have created one in the.pem format on the previous step. Use OpenSSL to convert the certificate. Run the command below.
- openssl pkcs12 -export -out C:\Certbot\keys\winrdp.pfx -inkey C:\Certbot\live\mydomain.com\privkey.pem -in C:\Certbot\live\mydomain.com\cert.pem -certfile C:\Certbot\live\mydomain.com\chain.pem -password pass:YOUR_PASSWORD
- certutil -p YOUR_PASSWORD -importPFX C:\Certbot\keys\winrdp.pfx noExport
Note: Replace YOUR_PASSWORD with your strong password.
8. Now apply the certificate to the Remote Desktop. Run the below command.
- thumbprint = (Get-ChildItem -Path Cert:\LocalMachine\my | WHERE {$_.Subject -match “mydomain.com” } | Sort-Object -Descending NotBefore | Select -First 1).Thumbprint
- wmic /namespace:\\root\CIMV2\TerminalServices PATH Win32_TSGeneralSetting Set SSLCertificateSHA1Hash=”$thumbprint”
9. Finally, use the instance IP address to establish an RDP connection to your instance. A notice about certificate validation need to be sent to you. Next, instead of using the IP address to connect to the instance, use the domain name. There shouldn’t be any certificate security alerts when you login.